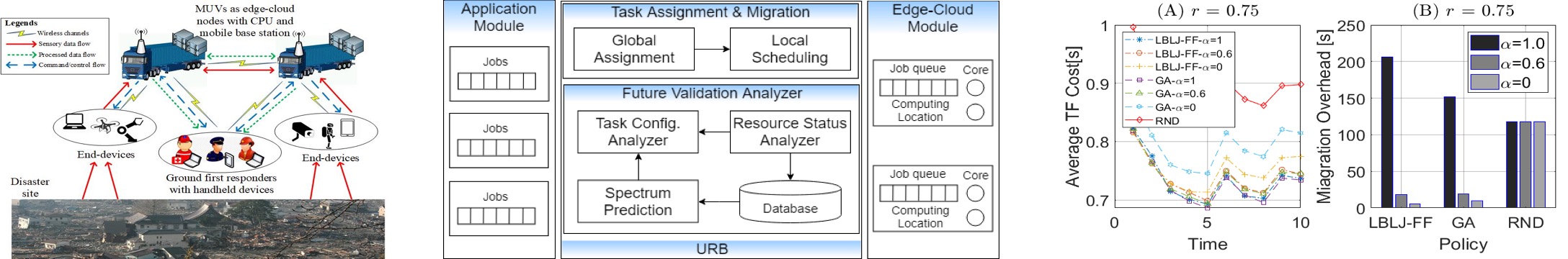
Software-defined fog computing for disaster response
Fog computing is distinguished from Cloud computing by not using resources contained in large remote data centers, but instead leveraging computation, storage, and network resources that are available as close to the user as possible. These computation resources may be, for example, a part of the communications network (Edge resources) that the user is connected to, rather than using that network simply to connect to the Cloud. For rapid situational awareness to first responders during large-scale disaster incidence response, Fog computing-based response systems can be more effective than Cloud-based systems because of this proximity. However, design of effective Fog-based systems for disaster response is non-trivial as generic Fog computing methods and models assume Cloud-like environment which cannot be applied for disaster scenarios.
This project proposes fundamental research, design, and development of a fog framework that is novel in tackling the unique challenges of Fog resource management for disaster incidence response. The goal is to make the fog framework resilient against an unpredictable system environment and agile in provisioning resources for mission-critical and real-time applications. Working closely with FDNY, the project is characterizing the fluctuations that occur during a large scale disaster and their impact . At the same time, the project is shifting the paradigm from traditional long-term cloud and edge resource optimization towards transient fog utility optimization under challenged environments. Using sate-of-the art, software-defined network and computing research and technologies, the project is designing genetic algorithms and deep learning algorithms that aim to optimize fluctuation avoidance without compromising limited fog resources. The outcomes of such optimizations in terms of algorithms are being implemented through design and development of a software-defined fog architecture with unified resource broker services.
Broader impacts:
The research will benefit: 1) disaster management efforts by the first responders, 2) incident response management planning and policy makers, 3) cloud, cyber infrastructure, network management, and future Internet research communities, and 4) faculty and students in cloud and network management classrooms and labs.The data generated in this project will be made available through digital repositories. The project related algorithms and software tools will, after publication, be made available under an open source license on GitHub. The proposed fog testbed will be made available to the broader cloud research community through integration with NSF supported PAWR testbeds.
Related publications:
-
Xiaojie Zhang, Amitangshu Pal, and Saptarshi Debroy,
EFFECT: Energy-efficient Fog Computing Framework for Real-time Video Processing,
IEEE/ACM CCGrid, 2021.
-
Xiaojie Zhang, Amitangshu Pal, and Saptarshi Debroy,
Deep Reinforcement Learning Based Energy-Efficient Task Offloading for Secondary Mobile Edge Systems,
IEEE LCN, 2020.
-
Xiaojie Zhang, and Saptarshi Debroy,
Energy Efficient Task Offloading for Compute-intensive Mobile Edge Applications,
IEEE ICC 2020.
-
Xiaojie Zhang, and Saptarshi Debroy,
Adaptive Task Offloading over Wireless in Mobile Edge Computing,
IEEE SEC 2019.
-
Xiaojie Zhang, and Saptarshi Debroy,
Migration-driven Resilient Disaster Response Edge-Cloud Deployments,
IEEE NCA 2019.
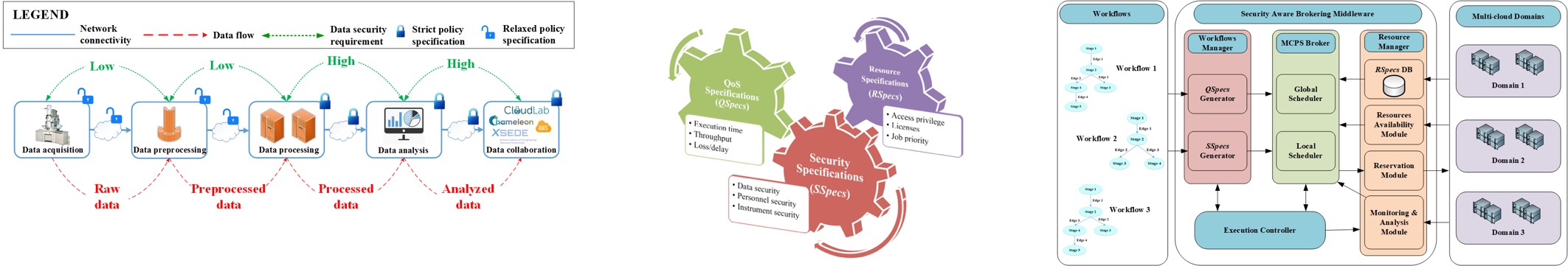
Security-aware multi-domain federated workflow management
Data-intensive science applications in research fields such as bioinformatics, chemistry,
and material science are increasingly becoming multi-domain in nature. To augment local
campus CyberInfrastructure (CI) resources, these applications rely on multi-institutional resources
that are remotely accessible (e.g., scientific instruments, supercomputers, public clouds).
Provisioning of such federated CI resources has been traditionally based on applications'
performance and quality of service (QoS) requirements. This project aims to augment
traditional resource provisioning schemes through novel schemes for
formalizing end-to-end security requirements to align security posture
across multi-domain resources with heterogeneous policies.
This project addresses the end-to-end multi-domain security design for
scientific applications by defining and formalizing security specifications along an application's workflow lifecycle stages.
The research work will advance the current knowledge for a CI engineer in the following areas:
(i) how to intelligently perform resource allocations among private and public cloud locations;
(ii) by streamlining end-to-end security posture across domains that are constructed via dynamic network services; and
(iii) how to "bring your own compute" programs in large facilities to reduce turnaround times in a secured and policy-compliant manner.
Broader impacts:
The resulting security formalization and alignment schemes will be implemented as a security middleware coupled within a unified resource broker framework that: (a) operationally integrates various software tools and systems such as perfSONAR, OpenStack, iRODS and Shibboleth; and (b) supports prototypes of web-portals and actual users (e.g., researchers and educators) within usability evaluation and validation experiments.
Related publications:
-
Mauro Lemus Alarcon, Minh Nguyen, Saptarshi Debroy, Naga Ramya Bhamidipati, Prasad Calyam, and Abu Mosa,
Trust Model for Efficient Honest Broker based Healthcare Data Access and Processing,
IEEE PerCom Workshops, 2021.
-
Minh Nguyen, Saptarshi Debroy, Prasad Calyam, Zhen Lyu, Trupti Joshi,
Security-aware Resource Brokering for Bioinformatics Workflows across Federated Multi-cloud Infrastructures,
ICDCN 2020.
-
Matthew Dickinson, Saptarshi Debroy, Prasad Calyam, Samaikya Valluripally,
Yuanxun Zhang, Ronny Bazan Antequera, Trupti Joshi, Tommi White, and Dong Xu,
Multi-cloud Performance and Security Driven Federated Workflow Management,
IEEE Transactions on Cloud Computing, 2018.
-
Ronny Bazan Antequera, Prasad Calyam, Saptarshi Debroy,
Longhai Cui, Sripriya Seetharam, Matthew Dickinson, Trupti Joshi, Dong Xu, and Tsegereda Beyene,
ADON: Application-Driven Overlay
Network-as-a-Service for Data-Intensive Science, IEEE Transactions on Cloud Computing, 2016.
-
Matthew Dickinson, Saptarshi Debroy, and Prasad Calyam,
End-to-End Security Formalization and Alignment
in Federated Data-intensive Application Workflows,
IEEE CLOUD 2016.
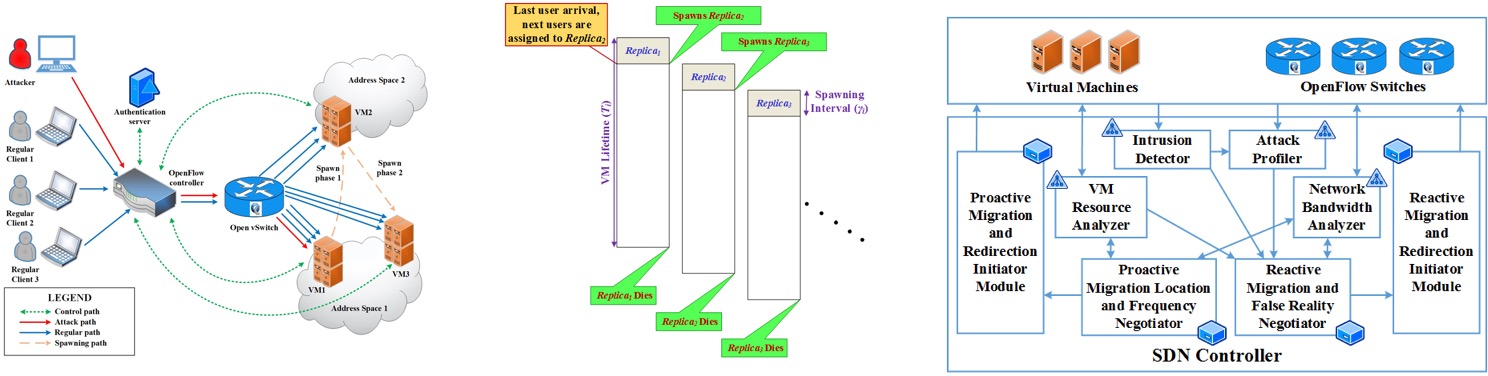
Moving target defense based agile cloud security
With the growing trend of hosting critical applications on cloud platforms, there is a need to protect these
applications from the security threats of cyber attacks. The network infiltration based attack defense
challenges within a cloud platform are more severe than traditional cyber security risks due to the
enhanced visibility of the cloud environment to the adversaries. The traditional 'detect-and-react' defense
techniques fall short in effectively ensuring Service Level Agreement (SLA) between the cloud hosted
services and their consumers. Thus, Moving Target Defense (MTD) based mechanisms can be explored as potential defense strategies due to their: a) fast
converging proactive and reactive maneuverability, b) amenability to adopt emerging network
management technologies such as, Software-defined Networking (SDN), and c) ability to create system
obfuscation and adversary deception. However, design of such MTD based defense strategy remains non-trivial.
In this project, we design a MTD based resilient cloud management framework that achieves dynamic proactive and reactive resource adaptations through placement and provisioning of cloud hosted applications among CSP resources instances at Internet speeds. The framework components collectively compute the best 'resource mapping', 'resource sizing', and 'adaptation frequency' in
order to optimize the application utility, and CSP cost. The research in this project leverages the awareness of: (a) statistical data analytics techniques, (b) threat assessment and modeling of clean and quarantined resources, (c) causal effect modeling with bayesian statistics, (d) evidence based
statistical trust modeling, (e) dynamic demand/supply based market-driven utility optimization under
multiple constraints, and (f) stochastic modeling based cost-benefit analysis and tradeoff design.
Evaluations are performed in terms of varied performance metrics based on simulation,
testbed, human subject survey, and cloud-scale implementation results.
Broader impacts:
The research methods, algorithms, results, developed software elements and tools will benefit: (i) cloud and
broadly cybersecurity researchers, (ii) cloud computing and Future Internet research communities, (iii)
cloud service providers, (iii) faculty and students in security classrooms and labs, (iv) cloud tenants, and
(v) administrators and consumers of cloud hosted applications. Experiences of deigning and
implementing the proposed framework will provide key insights to other scientific high
performance computing communities, such as CyVerse, and XSEDE, and other service providers that want
to design and implement cost-effective and resilient attack response mechanisms within their private
cloud environment.
Related publications:
-
Saptarshi Debroy, Prasad Calyam, Minh Nguyen, Roshan Lal Naupane,
Bidyut Mukherjee, Ajay Kumar Eeralla, and Khaled Salah, Frequency-Minimal
Utility-Maximal Moving Target Defense against DDoS in Cloud, IEEE Transactions on Network and Service Management, 2020.
-
Minh Nguyen, Amitangshu Pal, and Saptarshi Debroy,
Whack-a-Mole: Software-defined Networking Driven Multi-level DDoS Defense for Cloud Environments,
IEEE LCN 2018.
-
Saptarshi Debroy, Prasad Calyam, Minh Nguyen, Allen Stage, and Vladimir Georgiev,
Frequency-Minimal Moving Target Defense using
Software Defined Networking,
IEEE ICNC 2016.

Cyber security summer school for women
Despite the growing demand and tremendous opportunities in the job market, cyber security remains an area where there is significant shortage of skilled professionals regionally, nationally and internationally. More than 209,000
cyber security jobs in the U.S. are unfilled, and postings are up 74% over the past five years. Although this
situation is dire, what is particularly alarming is that women's? representation in this traditionally male-dominated
field of security is alarming. According to the Women?s Society of Cyberjutsu, only 11% of cyber security
professionals worldwide are women. In this U.S. alone, 50% of professionals are women, while 25% of computing
professionals are women. There is tremendous potential for women to become cyber security professionals, a market
of which is expected to grow from $75 billion to $170 billion by 2020.
A major reason for this gender gap in cyber security is the lack of recruitment and retention of college Computer
Science and technology-related female students. At CUNY, e.g., the recruitment and retention rates of such female
students are significantly lower.
I organize an annual two-week long summer camp at Hunter College. The summer camp will host incoming women sophomore students who: a) have not taken introductory computer science during their freshman year, b) have not yet declared their major, and c) have strong interest in pursuing computer science. The objective is to prepare and motivate them to register for introductory computer science course in the following fall semester and create path towards major/minor. It's FREE, click here to join now!






